Software-Defined Security
Overview
Operational security mechanisms in Information and Communication Technology (ICT) systems are currently facing challenges in dealing with new network threats and attacks. Software-Defined Security (SDS or SDSec) has been proposed to meet such challenges. It is a generic security model within which information security is controlled and managed by security software. The well-known functions of network security devices, such as firewalling, intrusion detection, access controls and network segmentation, are extracted from hardware devices and framed into a software layer. Protection is based on logical policies which are no longer tied to any security device [1].
The architecture of SDS is designed to be modular, scalable and secure [2]. Security data and control planes are separated, hence automating detection and protection using standardised control messages [3].
The architecture organisation follows three layers [4, 5]:
- The Physical Layer: this is at the bottom of the three-tier hierarchy, known also as the data layer or base layer. It contains hardware-forwarding devices such as switches, routers, virtual switches and access points.
- The Control Layer: this handles all the control and management operations. The security mechanisms are abstracted from the security devices: they sit inside the controller in the control layer. Security solutions that are normally implemented in the control layer include anti-virus, firewall, anti-spam and intrusion prevention system (IPS).
- The Application Layer: this contains software-defined networking (SDN) applications. Network security techniques can be deployed as applications in this layer. To be effective, security must be built into the architecture and must protect the availability, integrity and privacy of information.
The key features and attributes of SDS [2, 3]:
- Abstraction: SDS abstracts security policies from the hardware layer. They are run within the software layer. Common security models are defined and can be deployed repeatedly.
- Automation: each asset or device in the system is deployed and put in a security trust zone automatically. This is performed manually in traditional security approaches.
- Flexibility: SDS is entirely software-based. The security policy is flexible, and security is available “on demand”. It is relatively easy to scale up and adapt to changes. It consistently enforces security policies across board irrespective of the location of the network systems.
- Concurrency control: network security controls (such as intrusion and prevention, network segmentation, firewalling, violation monitoring, etc.) work together concurrently. Such an orchestration improves security and reduces the cost.
- Visibility: because security can be virtualised, network professionals can discover abnormal activities that would not be possible with physical devices.
- Portability: SDS allows for assets to carry their security settings with them as they scale or move from one location to another.
Application fields:
- Efficient and dynamic mitigation of security threats and attacks;
- Abstraction of security away from hardware vulnerabilities to overcome the cybersecurity issue;
- Hardware cost reduction, due to the virtualisation of the network security applications in commodity hardware;
- Utilisation of existing network appliances, even if they do not support advanced traffic monitoring mechanisms;
- Dynamic configuration of existing network nodes to mitigate against attack;
- Harmonised view of logical security policies, which exist within the SDN controller model and are not tied to any server or specialised security device;
- Visibility of information from one source;
- Integration with sophisticated applications to correlate events in a simpler manner and respond more effective and intelligently to security threats; and
- Central management of security, which is implemented, controlled and managed by security software through the SDN controller.
Shaping SDN in the cloud environment uses the SDS components to address the following challenges:
- The security levels within the infrastructure, control and application layers;
- The foreseen attacks within these layers;
- The actual security state; and
- The preventive and mitigation measures to effectively address the security issues raised by the analysis.
Benefits
The functionalities of SDS lead to the following benefits [6]:
- Simplicity: the security architecture of physical data centres is complex, because of requiring multiple servers, specialised hardware devices (i.e. Firewall Appliances, Hardware Security Modules), and network identities, etc. SDS supports the protection of information flows anywhere they reside.
- Automation: SDS allows for automation as it is independent from rigid hardware. For instance, encryption can be automated across virtual servers, availability zones or geographical regions.
- Scalability and Flexibility: Geography becomes irrelevant in securing networks with devices in multiple locations.
Operating three functional blocks pinpoints the link between SDS tools and SDN in future ICT systems such as cloud environments. SDS introduces simplicity to network security. However, SDN must immediately be followed by SDS as the foundation for software-defined data centres.
The European Cyber Resilience Act (CRA) is a legal framework that describes the cybersecurity requirements for hardware and software products with digital elements placed on the market of the European Union. End devices such as smart cards, smart meters and mobile devices exploited by TSOs undergo CRA [7].
Current Enablers
Three components are integrated to protect the network, as schematised in the diagram above. They are the enablers of SDS.
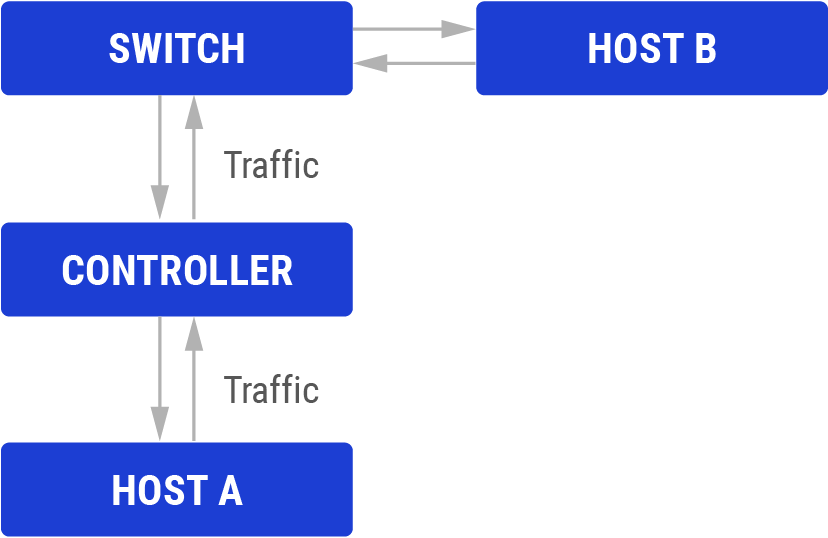
- Host: the host aims to send or receive data through the network. In traditional networks, security techniques reside in the host. The host checks new packets to see if they have threats. For the SDS, all security techniques are transferred to the controller.
- Controller: the controller is fully software based. All security checks are done inside the controller. The controller must have efficient access control by stating which types of packets should be carried within the network. It has visibility of the traffic flows and collects and processes information about the network.
- Switch: the switch consults the controller to decide whether to accept or reject a request. The current switches have limited storage capacity and cannot store all the rules. A reactive caching mechanism is adopted in SDN. However, this makes switches vulnerable to Denial of Service (DoS) attacks [8].
This generic approach can address the major components of a complex ICT system. Subsequently, the Software-defined System is split into five major components:
- Software-defined Networking (SDN);
- Software-defined Cloud Networking (SDCN);
- Software-defined Storage (SDS);
- Software-defined Data Centre (SDDC); and
- Software-defined Radio (SDR)
Each hardware component of the considered ICT system is scanned involving the three-tier approach (Host, Controller, Switch), which constitute the enablers of SDS.
R&D Needs
Further R&D activities should cover the following topics:
- Security automation in Software Defined Networks [9]
Security challenges on SDN planes [10] (attack types):
- Distributed Denial of Service (DDoS) Attacks
- Address Resolution Protocol (ARP) Spoofing Attacks
- Flow Rule Conflicts
- Weak Authentication and Communication Attacks
- Flooding Attacks
- Saturation Attacks
- Information Disclosure Attacks
- Tempering Attacks
- Scanning Attacks
- Man-in-the-middle (MIM) attack
- Cache Poisoning Attacks
- Control Channel Hijacking Attacks
- Cyber Attacks
- Disrupting the operation of an Internet of Things (IoT) system can be realised by a simple yet effective attack – malicious packet-modification attack (MPA) – that was previously identified in IoT based on wireless sensor networks.
The technology is in line with milestone “Development of restoration plans and update of pan-EU system defence plan” under Mission 3, milestones “Innovative cyber security approach for control centres” and “Integration of PMU (WAMS) in dynamic security assessment process” under Mission 4 of the ENTSO-E RDI Roadmap 2024-2034.
TSO Applications
Industrial (TSO included) papers or reports on applications of SDS solutions to address hot security topics are not made public for obvious reasons. However, a recent review has analysed and ranked the commercial security solutions available in 2023 [10]:
- SDN is established as a widely used concept in networks and has been introduced into the network architecture of IoT.
- Policies bound to workloads, such as virtual machines, containers, applications, services or microservices have been analysed.
- The ability to measure network workloads to ensure the confidentiality, integrity and availability (the Security Triad) of the services they are delivering has been analysed.
Examples
| Location: Slovenia | Year: 2023 |
|---|---|
| Description: TSOs may benefit from OT software-defined networking. SDN decouples the network management and switch configuration functionality from the switch hardware and places it into a centralised SDN controller. OT SDN mitigates risks by providing a completely deny-by-default data plane. It allows for a zero-touch deployment approach to designing a secure network with repeatable and predictable behaviour. | |
| Design: Construction of a new 400/110 kV substation and new 400 kV power lines to Hungary and Croatia by the ELES Transmission System Operator (TSO) from 2018 to 2022, accompanied by SDN and IEC 61850 station bus deployment. | |
| Results: SDN network switches can be configured to communicate only with an intended SDN controller and prevent users from connecting another SDN controller to the network for any malicious intent of changing or manipulating settings. | |
Technology Readiness Level The TRL has been assigned to reflect the European state of the art for TSOs, following the guidelines available here.
- TRL 8-9 for industrial applications.
- TRL 7 for the TSO context.
References and further reading
H. Tu et al., “A scalable flow rule translation implementation for software defined security”, Proceedings of Asia-Pacific Network Operation and Management Symposium, 2014.
M. N. O. Sadiku et al., “Software-Defined Security,” (2016) IJERAT, Vol. 2, no. 10, p. 13, 2016.
L. Wenmao et al., “SDN oriented software-defined security architecture,” J. Frontiers Comp. Sci. & Tech., vol. 9, no. 1, pp. 63–70, 2015.
A. Darabseh et al., “SDSecurity: a software defined security experimental framework,” Pro. IEEE Workshop CCSNA, pp. 1871–1876, 2015.
L. Yanbing et al., “SDSA: a framework of a software-defined security architecture,” China Communications, vol. 13, pp. 178–188, 2016.
“The benefits of software defined security”, e-spincorp.com.
M. Dabbagh et al., “Software-defined networking security: pros and cons,” IEEE Communications Magazine, pp. 73–79, June 2015.
N. M. Yungaicela-Naula et al., “Towards security automation in Software Defined Networks,” Computer Communications, vol. 183, pp. 64–82, 2022.
ENTSO-E, “ENTSO-E Research, Development, & Innovation Roadmap 2024-2034”
M. S. Farooq et al., “Security and Privacy Issues in Software-Defined Networking (SDN): A Systematic Literature Review,” Electronics, vol. 12, no. 14, p. 3077, Jul. 2023.
 ENTSO-E
ENTSO-E